Dataplane.org 2023 Q4 Newsletter
2023 Recap, Apache Struts NETINT, the year in SSH passwords
2023 was an interesting year for Dataplane.org. We were busy with multiple infrastructure projects, saw supported projects take shape, began developing our fundraising activities, and honed our educational mission with various community outreach opportunities. Here are some of what was new for us in 2023:
Migrated core infrastructure from a SOHO to 3rd party data centers and systems.
Moved one of our public-facing web and mail back-ends to a new provider.
Deployed the HTTP(S) sensor module and associated signals collection.
Grew our distributed network to over 500 vantage points.
Streamlined our vantage point management system.
Introduced the DNS type/name signals feed.
Began transitioning bill payment and collection into corporate accounts.
Delivered a talk on our sensor network at the FIRST Regional Symposium.
Provided infrastructure for a peer-reviewed research project (under submission).
And of course we continued to periodically highlight our activities and insight through this newsletter and other media channels. While we hope these newsletters supply interesting information, we are always open to suggestions for improvements. Feel free to reach out through our contact page, or support our work with a donation.
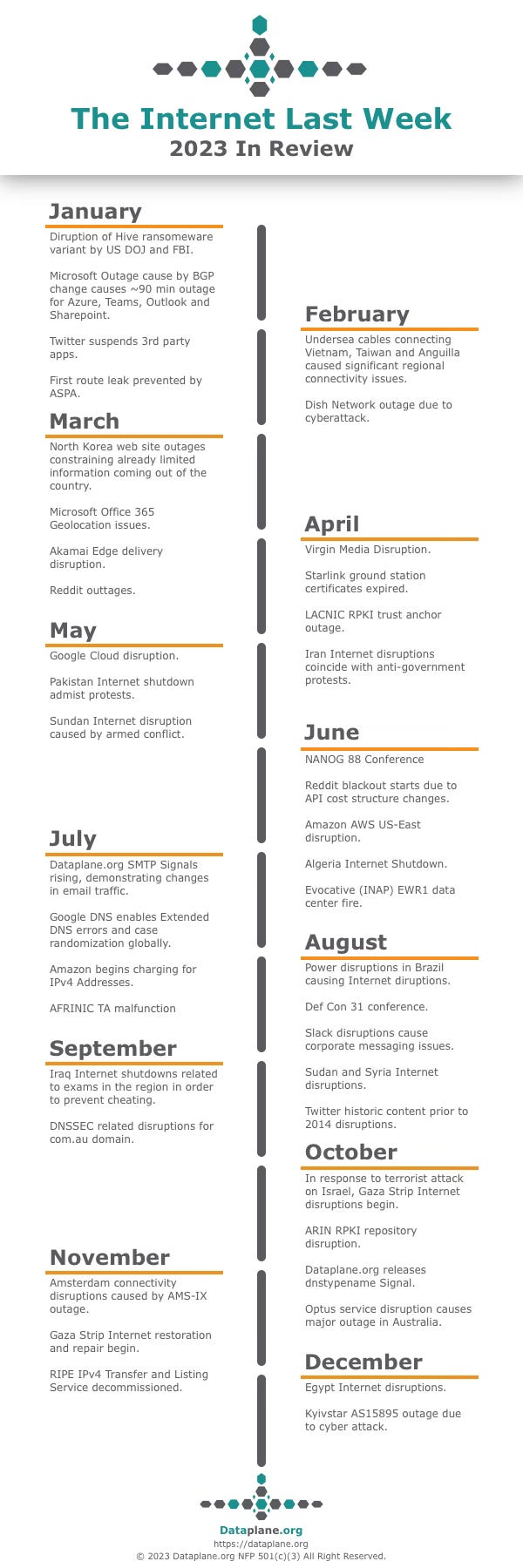
The Internet Last Week 2023 In Review
We’ve been publishing The Internet Last Week throughout 2023 and thought a summary of notable events from 2023 was appropriate for an end of the year newsletter. How many of these events do you remember?
2023 Secure Shell (SSH) Authentication Attempts
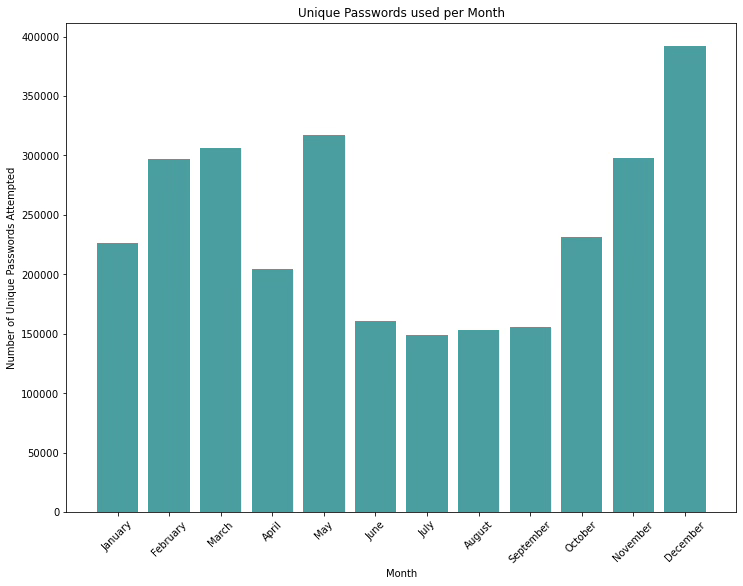
A year ago we looked at SSH activity in 2022 (Dataplane.org 2022 Year In Review) and saw some interesting things going on with SSH login attempts. Looking at 2023 data, we’ve noted some similar new developments. We observed significantly more events in 2023 than 2022. This can be explained in part by the growth of our sensor network. The plot below shows the raw count of unsolicited, unique password authentication attempts on our SSH sensors in 2023.
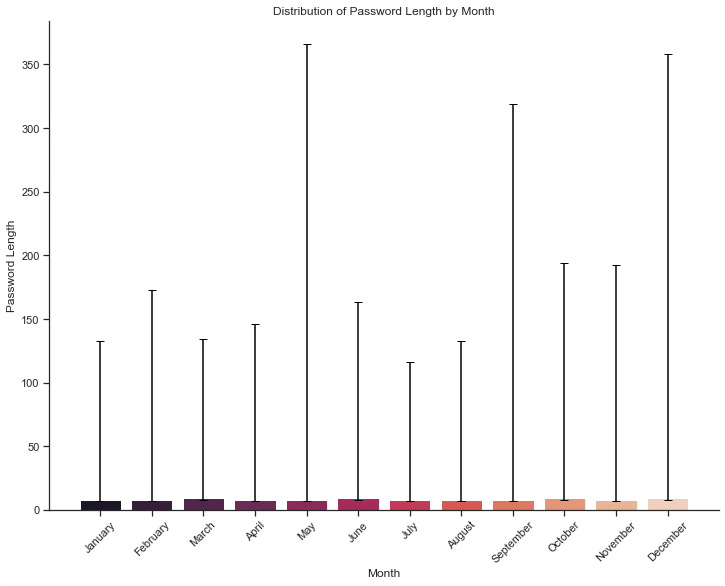
In 2023 SSH passwords attempted ranged from a single character to the suspiciously long 358 character password while the median was just eight characters on any given month:
Aggregating the unique passwords by closest matches to strings using a statistical model supplied by difflib, we identify the top passwords generalized in 2023 as follows:
Number 10: A@0599343813A@0599343813A@0599343813 (new to top 10)
Number 9: 1 (9th in 2022)
Number 8: 111111 (10th in 2022)
Number 7: qwerty (7th in 2022)
Number 6: 123123 (new to top 10)
Number 5: root (6th in 2022)
Number 4: test (5th in 2022)
Number 3: admin (3rd in 2022)
Number 2: password (2nd in 2022)
Number 1: 123456 (1st in 2022)
A word cloud for the entire year including unique values which are iterations of the top 10 list:
A look at the top unique entries over the months of the year:
Other common passwords we noted in our investigation, similar to 2022, were attempts with guest, changeme, raspberry, ubuntu and oracle. We urge any administrators to ensure they are not using default passwords on any of their devices, especially before connecting to the internet. A majority of the unique and extraordinary long attempts were a combination of unicode or ascii escape sequences attempting a remote exploit.
Apache Struts Vulnerability NETINT, Sort Of
One of our objectives is to develop and educate the Internet community about network signals intelligence (NETINT). As a relatively small non-profit, we have focused on the ability to develop the raw intelligence through our global network of sensors and probes with automation. If we had the resources we might devote more time producing unique in-depth analysis on all the data and trends at our disposal. For now at least, we’ve let others lead that charge either through the use of our data or their own. However, on occasion, particularly after the rush to be first-to-blog about a new network phenomenon or vulnerability we look to see if we have something new to add, highlighting how our visibility might be compliment the research of others. This is one of those times. Or is it?
In early December 2023 the Apache Software Foundation publicly disclosed CVE-2023-50164 - a Struts 2 remote code execution (RCE) vulnerability. Struts is a widely used web application framework and can be found in use on many public web sites. A number of threat intelligence researchers published their initial analysis and findings about the vulnerability and exploits seen in-the-wild. We won’t recap all the intricate details so we’ll refer readers to two that we like: Akamai’s Observed Exploit Attempts of Struts 2 S2--066 Vulnerability (CVE-2023-50164) and Trend Micro’s Decoding CVE-2023-50164: Unveiling the Apache Struts File Upload Exploit.
As part of an unrelated funded project we began monitoring HTTP and HTTPS activity earlier this year. We should be able to see some unsolicited Struts exploit attempts sent to random systems such as our sensors. What we have we seen? Almost nothing.
Initial exploitation attempts are reportedly performing reconnaissance to first determine if the Struts framework is running. If found, then the path traversal exploit is attempted. We do not run nor mimic the Struts framework on our sensor deployments. However, we have seen many POST requests for the “upload.action” file, but as far as we’ve determined these attempts are all for unrelated vulnerabilities or from threat intelligence service scanning operations.
We primarily see two types of activities related to the upload.action file. One is for an older file upload vulnerability in HIVISION products. These POST requests are for the /eps/resourceOperations/upload.action resource that come with the MicroMessenger UserAgent string. This activity dates back long before the recent Struts vulnerability disclosure.
The other noteworthy, unsolicited request for the upload.action resource we’ve seen originates from the Russian threat intelligence startup CyberOK not long after the Struts vulnerability was announced. CyberOK appears to be surveying only Russian geo-located IP address ranges and they do not appear to be attempting to exploit the service, but simply to test for it’s existence. Usually this type of behavior is done by national CSIRTS for the purposes of alerting and reporting. We have not seen CyberOK scan any other IP address ranges in other countries where we have sensors, including those in Ukraine.
While we cannot add positive evidence of Struts exploitation seen in-the-wild on unsolicited, unadvertised sensors, the lack of that activity is insight of a sort.
Our Future with Substack
In recent weeks Substack has come under fire for its position on certain types of activity it has become host to. This may be our last entry on the platform as we consider our options. Stay tuned.
Dataplane.org Updates
As we look forward to 2024 we look back on all the headway we made with our infrastructure. We are much better positioned to deploy new signal feeds, new types of measurement, and new types of insight. There were a number of things we left unfinished or haven’t started like we hoped to. Some of what we do is often dictated by pressures of time and resources. The organization is still operating on a very modest budget. While we have reached a level of funding that just about pays the bills in the year ahead, the operational cost incurred through time and energy of the founders goes unpaid. We are looking for ways to significantly increase our ability to fund this human capital so that Dataplane.org can really thrive through new services and innovation.
For contributions to our mission, to support our Signals availability, and to help us take on new projects, please consider contributing a donation.
We welcome feedback on any items covered in our update or suggestions for improvement.
Feel free to reach out via email, Mastodon, or on our Slack space (request an invite if you need one).