Dataplane.org 2022 Year In Review
2023 Q1 Insights
At the beginning of the year, we started with the idea of potentially moving towards a quarterly newsletter and wanted to get 2023 started with a look back at 2022. While we are a bit late publishing this, we felt it was important to ensure we could sift through the 585GB of data we collected throughout 2022. Reflecting on the prior year was a great way to focus on what went well, what could have gone better, and what to avoid in the next 12 months:
We welcomed Bill Eaheart to the team.
Continued to update our website.
Moved our social presence over to mastodon (https://fosstodon.org/@dataplane)
Launched our weekly microblog ‘The Internet Last Week’.
Bolstered our backend infrastructure.
On the newsletter, we launched 10 monthly newsletters vs our goal of 12.
Readership grew steadily throughout the year from ~15 to 67 readers.
Reached over 2,000 views.
Presented at 3 conferences: CHI-NOG, a REN-ISAC webinar, and the TF-CSIRT/FIRST Regional Symposium.
We’ve also expanded our fundraising efforts and brought in some funds to help ease our operating expenses. Now let’s reflect on last year’s activity and finish with some organizational updates.
The Year in Unsolicited Insights
The Dataplane.org network consists mainly of passive sensors which accept unsolicited traffic, Internet Background Noise, to generate our Signals. Our unique deployment allows us to cover a unique perspective with well over 300 servers across over 100 /8 network blocks in 6 continents. After combing through the data, we want to highlight some things seen across the Internet in 2022.
Domain Name System (DNS) Queries
As the phonebook for the Internet, DNS provides a unique perspective on what various scanners, probes, and misconfigured systems are looking for online. We will provide a deeper dive into future newsletters as we uncover more nuggets that would interest the public. For a summary view, it is interesting to look at the top 10 unsolicited queries from 2022:
Number 10: A.b.qnamemin-test.nlnetlabs.nl - research
Number 9: a.a.a.ooooops.space - possible scanning effort.
Number 8: procrastitees.com - defunct malware site.
Number 7: ip.parrotdns.com - possible scanning effort.
Number 6: www.google.com - possible scanning effort.
Number 5: VERSION.BIND and version.bind - - possible scanning effort.
Number 4: mz.gov.pl - possible DNS amplification attempt.
Number 3: . - possible DNS amplification attempt.
Number 2: ferc.gov - possible DNS amplification attempt.
Number 1: sl - possible DNS amplification attempt.
While www.google.com is expected to be high on the list, other interesting tidbits exist. The top unique names, with the lowest number of attempts throughout the year, belonged to measurement projects such as openresolve.rs and dnsmeasurement.com. We will continue to investigate some of the other unique query attributes and interesting queries.
Secure Shell (SSH) Authentication Attempts
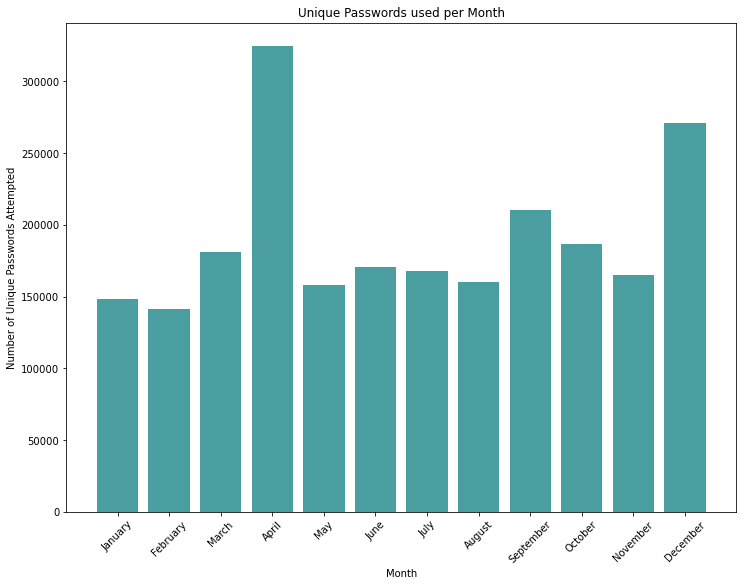
With Telnet and SSH being the most common remote management tool, we find it interesting to dive into the unsolicited authentication requests made via SSH, which is more secure when used appropriately. Across the year, we saw quite our fair share of attempts to login to our passive servers via SSH. The amount of unique passwords seen by month in 2022:
These passwords ranged from a single character and the longest password attempted 377 characters long! The median was an expected length of 8 on any given month:
Aggregating the unique passwords by closest matches to strings using a statistical model using difflib helped us identify the top passwords generalized in 2022:
Number 10: 111111
Number 9: 1
Number 8: 1qaz2wsx
Number 7: qwerty
Number 6: root
Number 5: test
Number 4: abc123
Number 3: admin
Number 2: password
Number 1: 123456
We generated a word cloud of the entire year:
Going through the entire data set, we could dive more closely into unique passwords in the top 10 by month. Here are a few examples:
January 2022 password variations:
June 2022 admin variations:
December 2022 test variations:
Other common passwords we noted in our investigation were attempts with guest, changeme, raspberry, ubuntu and oracle. We urge any administrators to ensure they are not using default passwords on any of their devices, especially before connecting to the internet. A majority of the unique and extraordinary long attempts were a combination of unicode or ascii escape sequences attempting a remote exploit.
Public Archive
We have been preparing our public archive and will provide data for the public to consume and utilize for research initiatives. Stay tuned to these newsletters for updates and additional insights.
Dataplane.org Updates
We have been building out our 2023 roadmap for features, infrastructure, and organizational updates over the past several months. In the next few months, we will prepare for tax season and work towards organizational updates to ensure we appropriately handle our current donations and future funding based on specialized reporting that we may provide for other organizations that align with our mission. We have also determined that a quarterly newsletter would better serve our community.
For contributions to our mission and our Signals continuous availability, please consider contributing a donation.
We welcome feedback on any items covered in our update or suggestions for improvement.
Feel free to reach out via email, Mastodon, or Slack (request an invite if you need one).