RPKI measurement & a SSH mystery
Also, new signal data and an organizational update
Friends, welcome to 2022 and the second edition of the Dataplane.org newsletter. The plan from here on out is to publish at least monthly on the first Monday of every month. This year will be one of rapid development so expect no shortage of things to talk about. We begin with a brief look at RPKI relying party (RP) measurement work that started last May, but was never formally introduced. Then, using longitudinal analysis of signal data we show a mysterious drop in SSH activity being observed around the globe. While on the subject, we take this opportunity to introduce new signal data named sshidpw, which is a daily report of SSH id/password pairs seen in the wild. We conclude with a summary on the state of Dataplane.org.
RPKI RP Measurement
One of the goals of Dataplane.org is to support the research of Internet systems, protocols, and security. Our work on the Internet routing system often covers all three aspects. Dataplane.org operates a “publication point” (PP), a component of the resource public key infrastructure (RPKI). You can think of a PP kind of like an authoritative DNS server. All RPKI relying party (RP) clients (akin to DNS resolvers) must regularly fetch all of the repository data stored on all available PPs. The RPs process the repository data and relay validated information to local routers so they can make informed decisions on the BGP routing announcements received from peers. The Dataplane.org PP was setup in May 2021 and a few months later we began publishing RP synchronization measurements every day since.
One of the more interesting observations from this data is how widely popular NLnet Labs Routinator is compared to all other observed RPs. There is nothing unusual about a piece of software dominating the market, but in the world of Internet infrastructure a monoculture can pose some risk. Digging a little deeper we can examine the diversity of RP software implementations per ASN. The chart below highlights how limited the diversity is. The vast majority of networks are running a single implementation, most likely Routinator. RPKI is still a relatively new addition to the Internet infrastructure so we’ll keep an eye on how RP software usage evolves.
SSH Activity Collapse in 2021
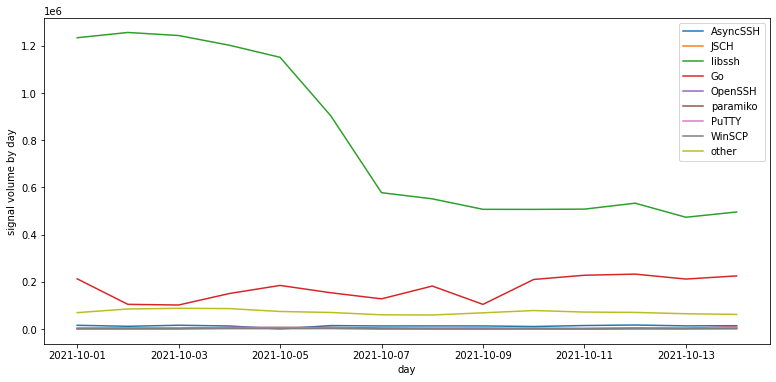
On or around October 6, 2021 our SSH client and password authentication signal data (SSH client activity shown below) observed what we would call a signal activity collapse. The shift was both dramatic and sudden as shown below. This phenomenon can also be seen from SANS port 22 traffic monitors and was independently confirmed with analysts from NETSCOUT ASERT. Not shown in the graph is that the collapse of SSH activity is observed widely across the globe and from a large number of unrelated networks. We have found no evidence of any take-down action or change in software that accounts for this anomaly.
Interestingly, the SSH software clients report in connection attempts show us that those using libssh have seen the most significant decrease. See the plot below.
When we brought these changes to the attention of colleagues a handful of explanations were proffered, but so far we’ve not seen compelling evidence for any definitive cause. Our best guess is that a new SSH worm has taken over a large proportion of infected systems, disrupting the probing activity we have been used to seeing. We would point to new attack campaigns such as this, this, and these two as possible explanations for a changing landscape. Perhaps if we could observe what those missing SSH client sources are doing now, their current activity can explain what happened? If we uncover anything further we’ll share our findings in a future newsletter. We would love to explore other data driven hypotheses, reach out to us if you have insights to share.
sshidpw
Speaking of SSH… Two of the most popular sets of signal data from Dataplane.org are based on our observation of unsolicited SSH client connections and SSH password authentication attempts in the wild. These are well known, persistent Internet threats. We are happy to announce the third in a set of SSH signal data. The SSH id/password signal data report (sshidpw) is a daily list of user name (aka ‘id’) and password pairs observed in SSH password authentication attempts on our sensors. Here is a sample, brief extract from a recent report:
...
sshidpw | root | 12345
sshidpw | root | 12345!
sshidpw | root | 12345!@
sshidpw | root | 12345-
sshidpw | root | 12345..
sshidpw | root | 12345^
...The columns of this pipe-delimited signal report from left to right are: category, id, and password. We believe the fields are self-explanatory, but see the full report for additional details. As of this writing there are over 60,000 id/password combinations observed per week!
Who is this for and why is it useful? System administrators might apply this data to user account credential auditing on their own systems. A researcher might use this for training data when analyzing user-selected credentials across multiple password-based systems. If you have other ideas on how to use this signal data you’d like to share with us, we’d love to hear about it. We may also be able to accommodate one-time requests that require only modest effort and modification for free if this signal data falls short of your needs.
The State of Dataplane.org
Our operating structure is still a work-in-progress. We have had an initial discussion with legal counsel, but nothing formal has yet begun. The good news is that our desire to operate as a non-profit appears to be both reasonable and attainable. While we wait for the process to commence we’ve been thinking about what goes into the organization’s official mission statement. We see ourselves as a supplier of signal data, analysis, tools, and measurements supporting operations and research in the areas of Internet infrastructure systems, protocols, and security. To the extent we can provide these things to the community, especially where no readily available alternative exists, this is what we aim to spend our time working on.
On the technical front we’ve added a handful of systems to the sensor pool. In addition we’ve acquired some new servers that will be used to maintain a historical public data archive, a redundant database, and query front-end. An initial API for querying our data has been developed and we are now building some new back-end components that will allow us to glue this code to our data repository. It may be awhile before we can make anything widely available to the public, but beta testing is not far away.
We’ve also been testing a new DNS module and enhancements to the TELNET and SIP modules, all of which we expect to be rolled out in the coming weeks. More automated measurement of our signal data, such as the type of graphs shown above, is also on our list of things to get out the door. Lastly, we have a Slack space that we’d like start inviting friends, benefactors, beneficiaries, and observers to. Keep an eye out for an invite in the future.
As always, we want to hear from you. Feel free to reach out with your reactions. Your feedback is the only way we can really know if what we’re doing is worthwhile or not.