Dataplane.org 2025 Year in Review
Quiet progress, new NTP feeds and a glimpse into 2025, SSH passwords and DNS radiation
2025 has been a busy year, and we have been quietly working through several different projects that will ultimately benefit the Internet community. The following is a summary of some of our activities and insights from the past year:
Three new Network Time Protocol (NTP) Signals (modes 3, 5 and 7) are now available from the Signals page.
We deployed a new IP4 anycast sinkhole network.
We began deploying multiple, diverse BGP route collectors.
We deployed new WWW and DNS sinkholes.
We set up new IP surveying (scanner) systems.
We deployed new and upgraded many backend, sensor, and probe systems.
We began the rollout of a new JSON-based WWW sensor collection system.
We performed a DNS service provider commissioned penetration test and audit.
We supported multiple academic research projects with data and systems.
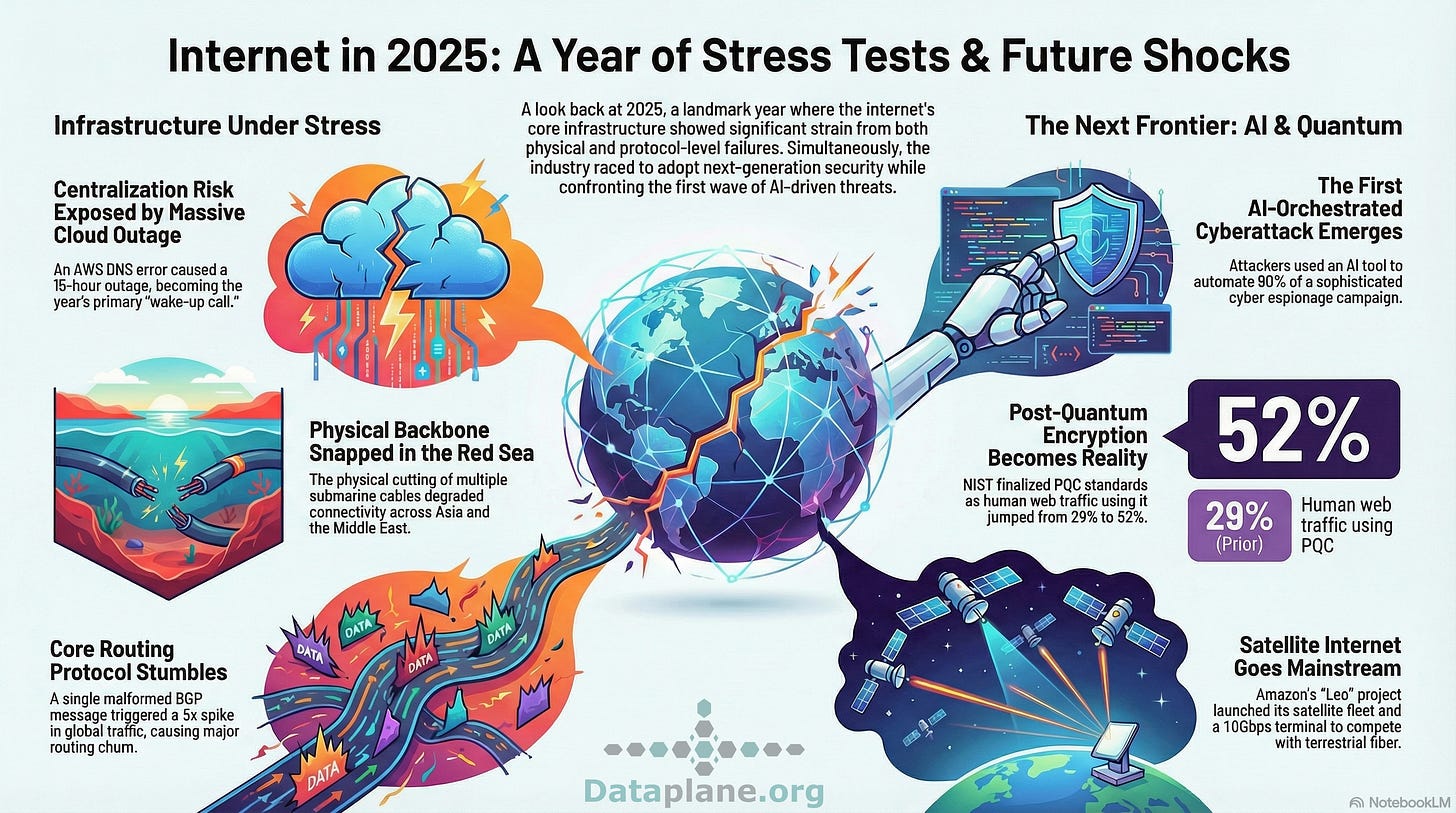
2025 Internet Operations & Infrastructure Events
January - ICANN declares RDAP is now the definitive source of gTLD registration information, sunsetting the WHOIS service.
February - Nationwide power grid failure in Chile demonstrated the Internet’s absolute dependency on physical utilities when a regional blackout occurred. Notable: PlayStation Network suffered a 24-hour failure, locking out 116M users.
March - In a claim widely disputed, Elon Musk attributes a Twitter outage to an attack originating from Ukrainian IP addresses. North Korean BGP routes were widely rejected due to a self-inflicted misconfigured RPKI ROA.
April - OpenSSL enables Post-Quantum Cryptography (PQC) by default. Amazon launched 27 production satellites for Amazon Leo (previously Project Kulper). Dave Täht, co-founder of the Bufferbloat project, passes away.
May - A malformed BGP message containing a corrupt prefix-SID attribute triggered automatic session resets in Junos and Arista implementations. Global message rates spiked from 30k to over 150k per second, causing significant routing churn.
June - A widespread Google cloud service disruption took down many services, including, for example, Gmail, Discord, and Spotify.
July - Cloudflare conducted a post-mortem on its 1.1.1.1. public DNS resolver incident highlighting Anycast routing vulnerabilities. USENIX holds its last annual technical conference. Starlink experiences a global network outage.
August - NIST finalized the first PQC standards, making them mandatory for federal systems. This coincided with Let’s Encrypt ending its OSP service. China’s GFW disrupts TCP port 443 traffic. Debian Trixie (13) released.
September - Multiple submarine cables (SMW4 and IMEWE) were cut near Jeddah, Saudi Arabia. This physical failure degraded connectivity across Asia and the Middle East, while Microsoft Azure users experienced signification latency during traffic rerouting. AFRINIC holds long-awaited board elections following governance issues.
October - Major Azure and AWS outages occur within weeks of one another. These two events garnered many reactions to question the US and single-vendor loud dependencies. dns0.eu service discontinued.
November - Anthropic disclosed the first AI-orchestrated cyber espionage campaign, where attackers used Claude Code to automate 90% of tactical breach work. Cloudflare experiences a major outage affecting many 3rd-party services.
December - RPKI ASPA objects begin to appear after RIPE enables the ability to create them in their dashboard. Cloudflare reported that 52% of human-initiated web traffic was PQC encrypted by early December, a massive jump from 29% in January. ARIN accidentally reallocates IP address resources. NIST atomic clocks experience a power outage.
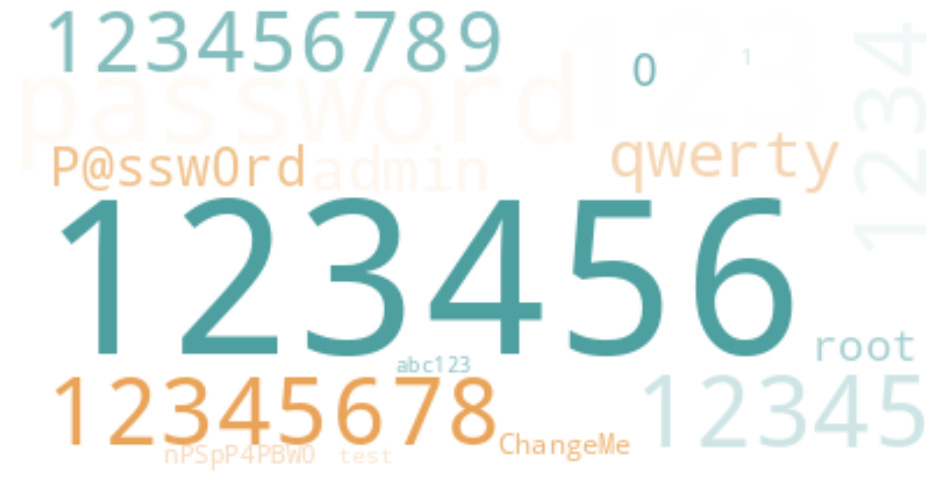
The Year in SSH Passwords
As we analyze the authentication attempts captured by our distributed network of vantage points, one trend remains undisputed: numeric sequences are the king of brute-force attempts. Throughout 2025, 123456 was the single most common password attempted, accounting for over 41 million attempted authentication attempts.
The top 10 passwords for the year were overwhelmingly simple:
123456 (41M+)
123 (13.7M+)
password (9.8M+)
1234 (9.3M+)
12345 (6.4M+)
12345678 (6.2M+)
admin (5.8M+)
P@ssw0rd (5.6M+)
1 (5.4M+)
qwerty (4.5M+)
While the “usual suspects” dominated the annual aggregate, we observed interesting monthly shifts. The year began with high volumes in January, where 123456 saw over 8.3 million attempts. We noted a distinct lull in mid-year volume; by July and August, the top count for the top password dropped to approximately 1.1 million per month.
However, volume surged aggressively in Q4. By November and December, counts for 123456 rebounded to over 5 million per month. We also spotted some specific campaign anomalies:
ChangeMe cracked the top 10 in February and March, suggesting targeted device defaults were attempting to be exploited.
test appeared consistently from April through June.
A highly specific complex string, nPSpP4PBW0, suddenly appeared as the 8th most common password in September, with over 174k attempts, likely indicating a specific botnet or targeted credential spray.
Unsolicited DNS Queries of 2025
Beyond authentication, our sensors monitored the noise of the Domain Name System (DNS). The top 10 unsolicited DNS queries for A records in 2025 highlight a mix of vendor-specific calls, internet scanning research, and common defaults.
The most frequent queries were:
cdn.samsungcloudsolutions.com (617k+)
ip.parrotdns.com (448k+)
google.com (307k+)
dnsscan.shadowserver.org (225k+)
ims.mnc001.mcc262.3gppnetwork.org (193k+)
testip.internet-census.org (171k+)
www.google.com (170k+)
xyz.example.org (152k+)
wikileaks.org (151k+)
example.com (116k+)
This list underscores the persistent background radiation of the internet, from automated checks (Samsung) to security research scanning (Shadowserver, Internet-Census).
Looking Ahead to 2026
As we move into 2026, Dataplane.org remains dedicated to our motto: “For operators, by operators”. We continue to maintain over 600 nodes across 65 metropolitan areas to ensure our vantage points for Internet infrastructure insight, such as the Signals feeds, statistics, and research reports, are trustworthy and reliable.
Leveraging much of the new work we began in 2025, we look to build on our capabilities to provide more data, more insight, and support more research in 2026.
Maintaining this infrastructure requires resources. We are a 501(c)(3) nonprofit organization, and we rely on the support of the community to keep our data free and tools available. If you find value in our signals, analysis, or reports, please consider a donation to help us sustain these efforts into the new year.
Here’s to a secure and robust Internet in 2026!